Electronic Security Solutions - ESSolution
When we talk about electronic security we think about cameras, ring, and access control, and that's it. No, this idea is far away from reality, at ED&TD® we take the concept further, and we include in the design of the solution engineering that provides real time control and a high level of cyber security, creating two concepts, viz:
Before we explain these concepts to you, we need to talk about what the components of an Electronic Security solution (ESSolution) are.
We also need to talk about how our engineers design an ESSolution.
After reading this, you will understand why ED&TD® is the best choice for implementing an electronic security solution in a small office/home office (SoHo) environment. Don't worry, residential sector—these concepts apply to you, too! Would you like to learn more about our electronic security portfolio? Or maybe you already know about it.[…]
Okay, let's start with the journey »
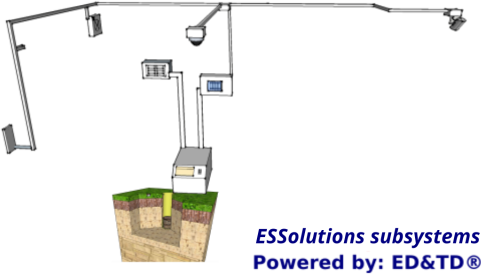
Components of an Electronic Security System
A well-designed ESSolution, regardless of the vendor, has 8 components or called too subsystems. These are:
- Subsystem 0 - Power Supply and Cabling Infrastructure
- Subsystem 1 - Network Infrastructure
- Subsystem 2 - Data Storage Infrastructure
- Subsystem 3 - Monitoring Infrastructure
- Subsystem 4 - Real-time control capabilities and high-level cybersecurity layer
- Subsystem 5 - Display Mode
- Subsystem 6 - Network Operation Center (NOC)
- Subsystem 7 - Telecommunication Room (TR)
The above subsystems are the theoretical framework of our ESSolution doctrine.
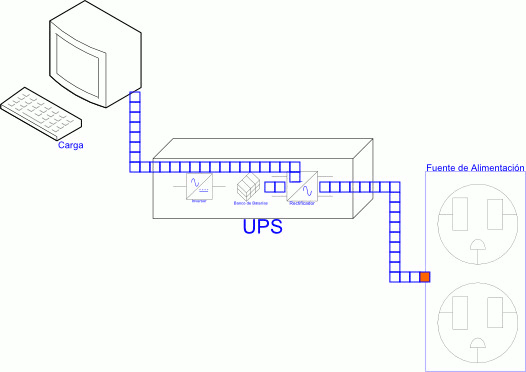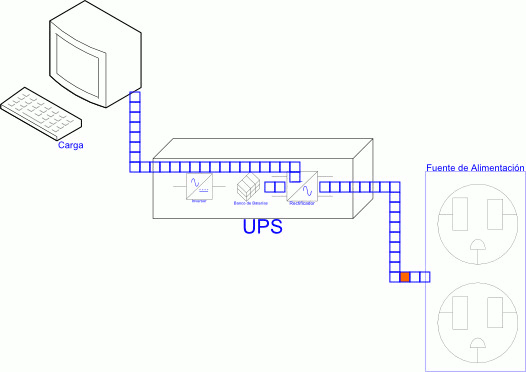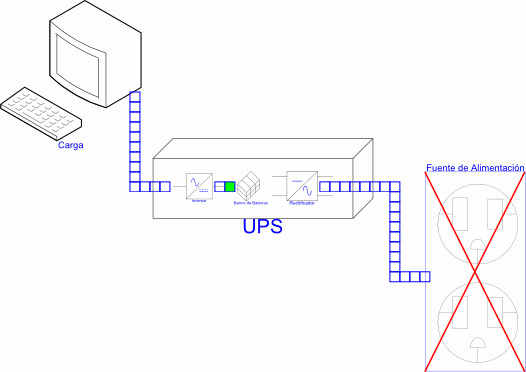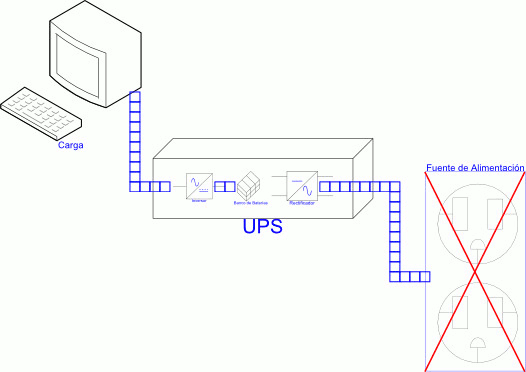
Subsystem 0 - Power Supply and Cabling Infrastructure
The ESSolution is a dedicated service, such as a fire alarm system that can never fail, where the branch circuit shall not supply other loads. NEC - Article 760.121 (B).
The above article, along with the articles 800, 805, 810, 820, 830, and 840 of the NEC, was our starting point when we designed the ESSolution, and per se it's the definition of the first subsystem, which we called Subsystem 0 - Power Supply and Cabling Infrastructure.
This subsystem is integrated for the following elements:
- Dedicated Branch Circuit from Main Panel.
- Grounding Electrode System.
- Uninterruptible Power Supply (UPS)
- Rack.
- Raceway.
- Cabling.
- Junction and Connection Boxes.
- Final Junction Boxes.
The Subsystem 0 is designed and implemented in accordance with the NEC, the Structured Cabling Methodology, and the Telecommunications Industry Association ANSI/TIA-568 standards for telecommunications cabling in commercial buildings.
Components of an Electronic Security System
Subsystem 1 - Network Infrastructure
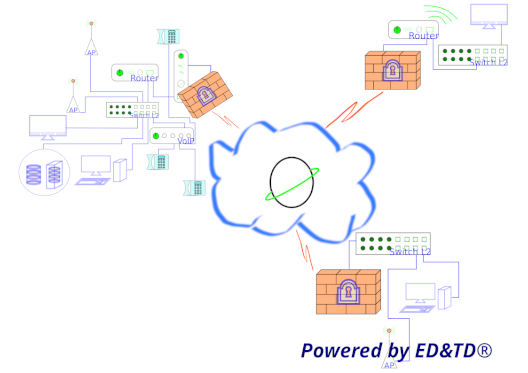
All of the devices and equipment needed to connect the monitoring devices to the data storage devices, such as the router, switch, access point, radios, and other specific equipment, integrated the Subsystem 1 - Network Infrastructure.
This subsystem includes all tasks required for network design and the implementation of the high-level cybersecurity layer.
Subsystem 1 - Network Infrastructure and Subsystem 2 - Data Storage Infrastructure are essentially the data center where all the data generated by the ESSolution is processed.Our ESSolution provides data centers from Tier 0 (non-standard) to Tier 4.
Components of an Electronic Security System
Subsystem 2 - Data Storage Infrastructure

There are three information storage technologies, namely:
- NVR - Network Video Recorder, works with surveillance equipment.
- SVR - Server Video Recorder, works with whole spectre of Monitoring Infrastructure.
- CVR - Cloud Video Recorder, it's a service provided by third party vendor, and usually works only with surveillance equipment.
The above mentioned technologies are designed to communicate over a network.
Also, you may have heard about DVR - Digital Video Recorder, our Monitoring Infrastructure doesn't work with this technology because it is very old.
Components of an Electronic Security System
Subsystem 3 - Monitoring Infrastructure

Monitoring Infrastructure is all the devices and equipments needed to surveillance, monitoring and control the requirements of our customers.
- The surveillance equipment are: Cameras, Doorbell, and Ring.
- The monitoring devices are: Access Control.
- The control devices are: Sensors, Transducers, and Actuators.
Each devices and equipmets have differents features that integration when our engineers design specific ESSolution.
The ability to communicate over a network is the most important feature of these devices and equipments.
Components of an Electronic Security System
Subsystem 4 - Real-time control capabilities and high-level cybersecurity layer

We have arrived at the core of our journey.
Depending on the customer needs when our engineers design a specific ESSolution they take the features of each spectre of Monitoring Infrastructure and integrate & make hardware, firmware and software in the specific ESSolution that will provide the perfect solution to our customer requirements.
Based on the capabilities of the Monitoring Infrastructure, our engineers can to do things like:
- Detect: People, vehicles, animals, and weapons. And trigger a specific event as required by the design.
- Turn on a flood light array when something crosses the intrusion area,
- Play a message when something crosses the set tripwire line,
- Zero (0) blind spots or dead angles,
- Face Detection & Face Recognition,
- People Counting
- and other specific actions.
When we talked above about of other specific actions or what our engineers can do, we were referring to triggering an event or being alerted anytime whenever a specific action occurs that we need to control.
So if you need to control certain events, you need to be able to do it in real time.This is it. And that premise is called Real-time control capability.
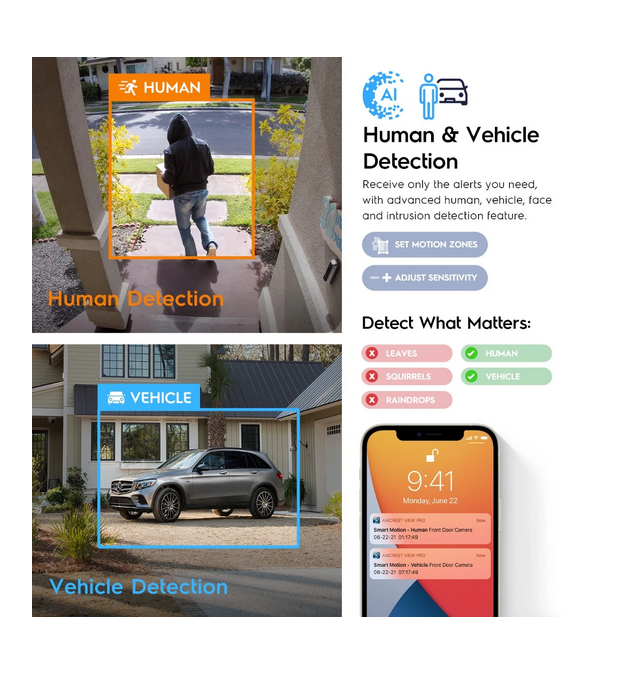 Human & Vehicle Detection
Human & Vehicle Detection
This is a special algorithm that uses the AI capabilities to send only the alerts that the ES solution needs, with advanced people, vehicle, face, and intrusion detection.
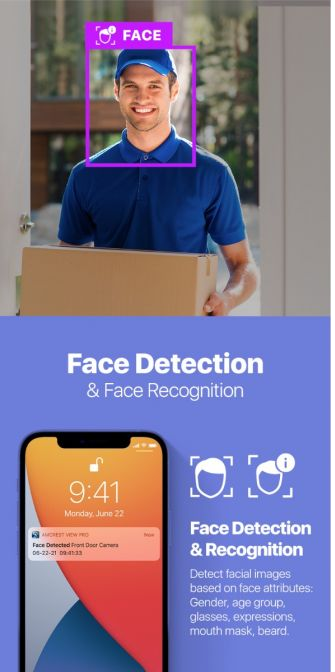 Face Detection
Face Detection
This process involves identifying the presence of a face in an image or video. It focuses solely on locating and recognizing the shape or outline of a face but does not associate it with a specific identity.
Our algorithm detect facial images based on face attributes such as:
- Gender
- Age group
- Glasses
- Expression
- Mouth mask
- Beard
 Intrusion
Intrusion
It's the specific area being monitored.
Intrusion as a perimeter protection technique.
The Perimeter Protection is the virtual fence created for security that triggers an event when motion is detected when the fence is crossed.
 Tripwire
Tripwire
It's like a fence with a defined perimeter.
Tripwire as a perimeter protection technique.
The Perimeter Protection is the virtual fence created for security that triggers an event when motion is detected when the fence is crossed.
 Face Recognition
Face Recognition
Facial recognition takes this a step further by recognizing the face and identifying or verifying the person based on their unique facial features. It compares the detected face with stored data in a database to match and confirm the person's identity.
We implement this technology using the following algorithms:
- Face detection.
- Face analysis.
- Image to data conversion.
- Find a match with stored data in a database.
- Make a decision after confirming the person's identity.
 People Counting
People Counting
This feature provides a statistic based on the number of people who entering and exiting a specified area.
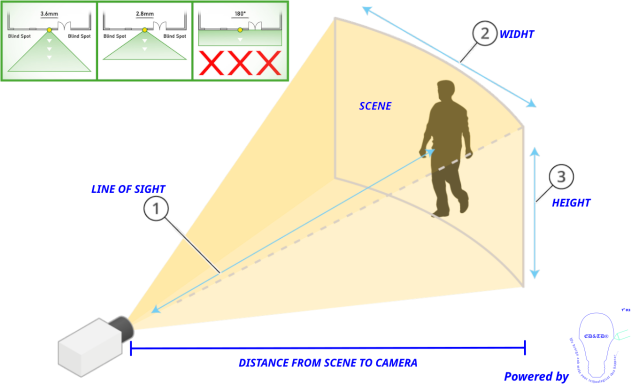 Zero (0) Blind spots or Dead angles
Zero (0) Blind spots or Dead angles
A camera's field of view is defined by the size of its lens. And by definition, the field of view is the extent of the observable world that is seen at any given moment.
What happens if your field of view doesn't show the full extent of what you see? In this case, when the extent of what you see is not shown for the camera's field of view, this unseen extent is called the blind spot or dead angle.

Now, the Monitoring Infrastructure has the ability to communicate over a network. This feature is a strength of our ESSolution but it is also our Achilles' heel. Let me explain:
When you connect any device or equipment to a network, you have a cyber breach. Why is that? Your device or equipment can be hacked, in the best cases it will generate fake alerts, but in the worst case it will not generate alerts to facilitate a robbery, or the hacker can download files like videos and photos and sell them on the dark web. This Achilles' heel is the reason why our engineers implement a High-level Cybersecurity Layer in the design of an ESSolution.
When we started this journey, we talked to you about two concepts, remember?.
These concepts are the result of this Subsystem 4 - Real-time control capabilities and high-level cybersecurity layer, because each concept have High-level Cybersecurity Layer and based on the Real-time control capability, our engineers implement one or another concept when designing the ESSolution.
All right, the concepts:
Components of an Electronic Security System
Electronic Security in Passive Mode (ESPM®)

Based on video surveillance, motion detection, access control, and smoke sensors, the ESPM® concept is the integration of these elements into a single control application.
We have an ESPM® solution. Read more about it …
Subsystem 4 - Real-time control capabilities and high-level cybersecurity layer
Components of an Electronic Security System
Electronic Security in Active Mode (ESAM®)
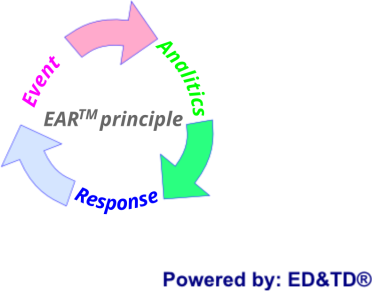
The ESAM® concept implements the EAR™ principle. This means:
Event -> It is defined as the action that disturbs the security of the area, sector, or zone under surveillance. In other words, it is the condition that triggers a final response. i. e: When a person, animal, vehicle or anything else crosses the set tripwire line or intrusion area.
Analatics -> It is the process of considering the impact level over the monitored area. Each event versus impact has a value called weighting, which is a stochastic process that provides a specific response. This process translates into an algorithm that must be encoded and encrypted using the same logic as the Monitoring Infrastructure it is being applied to. This algorithm implements several techniques, namely:
- Digital image processing for facial recognition.
- Comparison patterns from digital speech processing.
- Biometric recognition algorithms.
- Matching patterns from digital input.
- Among others...
Response -> It is the action that is taken in response to the event.

In essence, the EAR™ principle is an algorithm that our engineers design and codify according to customer needs.
For example, in this case (image on the right), when the camera sensor detected one or more people at the pool edge, the algorithm triggered three alarms, one on the loudspeakers in the pool area, the second on the monitor in the NOC, and the last in the app.
Let us show you in detail how the EAR™ principle works in this case:
Event: One or more people at the pool edge.
Analitics: The pool edge is defined as a tripwire line. In this context, when the tripwire line is triggered, a comparison process determines the distance between the pool edge and the each person, assigning a unique value to each distance, this value is called weight. This weight is used by a risk scale to make a decision about the specific situation.
Response: In this case, the risk is higher, so the response triggered three alarms, one on the loudspeakers in the pool area, the second on the monitor in the NOC, and the last in the app.
In the example above, the camera has an AI feature, so the algorithm was coded and encrypted using AI.
We have an ESAM® solution. Read more about it …
Subsystem 4 - Real-time control capabilities and high-level cybersecurity layer
Components of an Electronic Security System
Subsystem 5 - Display Mode
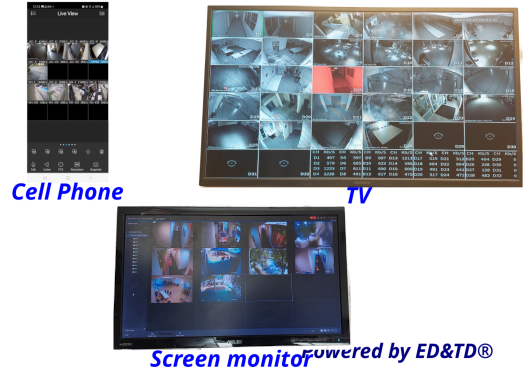
Ability for multiple devices and multiple user accounts to view the area, sector, or zone being monitored and the surveillance, is called Subsystem 5 - Display Mode.
- Devices from which you can view monitoring or surveillance:
- TV
- Screen monitor
- Cell Phone
- Tablet
- Each ESSolution supports from 1 to 15 user accounts.
- Each user account can easily be logged on to any device at the same time.
Devices, user accounts, and logon capabilities are the hallmarks of this subsystem.
Components of an Electronic Security System
Subsystem 6 - Network Operation Center (NOC)

Network Operation Center - NOC, such as Subsystem 6, is the heart of the solution once implemented.
The NOC is where you have total control over your Electronic Security Solutions - ESSolution.
The NOC complies with Subsystem 0 - Power Supply and Cabling Infrastructure, Subsystem 1 - Network Infrastructure, Subsystem 2 - Data Storage Infrastructure, and Subsystem 5 - Display Mode.
We identify each subsystem in the image at right:
- Subsystem 0 - Power Supply and Cabling Infrastructure » The Rack containing the surge protector, path panel, and other power and cabling infrastructure.
- Subsystem 1 - Network Infrastructure » Shown on the Rack containing the Route-d, switch and other network devices.
- Subsystem 2 - Data Storage Infrastructure » It's the NVR/SVR.
- Subsystem 5 - Display Mode » The Monitors.
Once ESSolution is deployed, you can monitor the entire solution from the NOC.
Components of an Electronic Security System
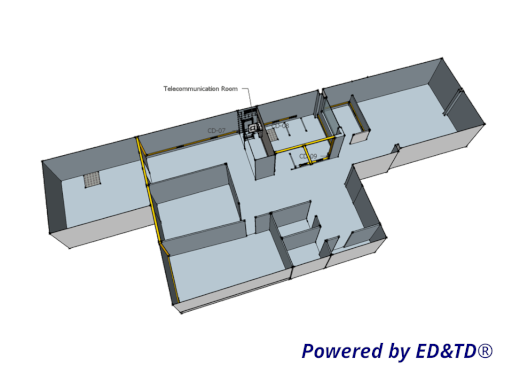
Subsystem 7 - Telecommunication Room (TR)

Subsystem 7 - Telecommunication Room (TR) is a helper subsystem for Subsystem 0 - Power Supply and Cabling Infrastructure, implemented when the Subsystem 0 - Power Supply and Cabling Infrastructure requires backbone cabling in your implementation.
Subsystem 7 - Telecommunication Room (TR) complies with Subsystem 1 - Network Infrastructure and Subsystem 0 - Power Supply and Cabling Infrastructure.
The image on the left shows the rack containing the switch, surge protector, path panel, and other network devices, power and cabling infrastructure.
Components of an Electronic Security System
How our engineers design an ESSolution
Our engineers used the ESSolution doctrine, which has three stages:
Pre-Sales Site Survey
At this stage, we collect all the information from our customers that will allow us to do what the customer needs in terms of security.
This information includes some data such as:
- Contact information
- A complete description of where the project will be developed
- Some technical notes that our engineer will see in the field and are design considerations
- Any documentation support
How our engineers design an ESSolution
Design stage
In the design stage, the Components of an Electronic Security System are implemented as a theoretical framework where they find a comprehensive guide to solve any requirement from the pre-sales site survey stage.
With this theoretical framework, our engineers convert the requirement into a design parameter to be solved by a specific subsystem.
How our engineers design an ESSolution
Installation stage
In the installation stage, the supply, installation and commissioning of the services and equipment that make up the solution are carried out by our engineers and technicians who are trained, qualified, certified and highly competent.
How our engineers design an ESSolution
 Electronic Security solutions on Passive mode - ESPM®
Electronic Security solutions on Passive mode - ESPM® Electronic Security solutions on Active mode - ESAM®
Electronic Security solutions on Active mode - ESAM® Amazing Doorbell Camera Solution - ADCS
Amazing Doorbell Camera Solution - ADCS Surveillance CCTV System - SCCTVS
Surveillance CCTV System - SCCTVS


Our Customers Comments
Knowledgeable, careful, pleasant to work with, patient, and reasonably priced.
One of the best investments in my life is the home system cameras. I travel a lot so I can monitor my house from different countries anytime. In November 2021 I had visitors from NYC and they parked their car on the street instead of my driveway. So when they were leaving the car disappeared, they thought their car was stolen but I doubt it. I went to see the recording in the cameras and noticed the tow truck took the car at 2:30 am and I could pause and zoom in to see the name of the company. I googled it and found out the company info. They recuperate the car in less than 2 hours. I am so glad to have cameras and see what's going on anytime.
Write A Comment or Request An Appointment For Check Your Next Electronic Security Project According Your Needs...