BSOD error in latest crowdstrike update
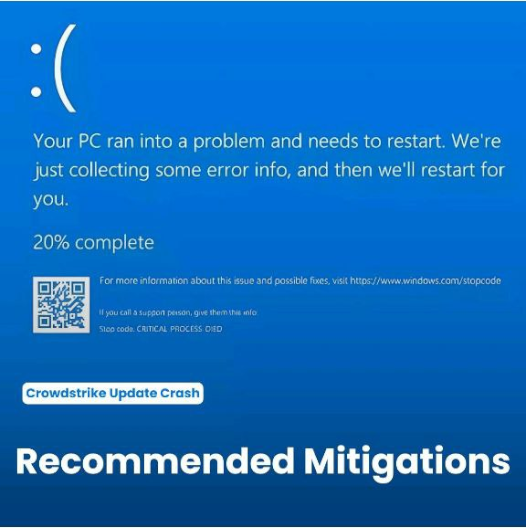
Late Thursday into Friday, reports began to emerge of IT problems wherein Windows computers were getting stuck with the infamous “Blue Screen of Death (BSOD)” — a bright blue error screen with a message that displays when Windows encounters a critical failure, crashes or cannot load.
"CrowdStrike is actively working with customers impacted by a defect found in a single content update for Windows hosts. Mac and Linux hosts are not impacted. This was not a cyberattack." CrowdStrike posted on its website.
Who is affected by this IT crash?
- Below is a detailed table listing the affected countries and services as of July 19, 2024.
Country Category Details Australia Media ABC, SBS, Seven Network, Nine Network Airlines Qantas, Virgin Australia, Jetstar Airports Sydney, Melbourne Supermarkets Woolworths, Coles Banks NAB, ANZ, Commonwealth Bank, Bendigo Bank, Suncorp Retailers and Fast Food KFC, self-checkout systems Canada Banks TD Canada Trust mobile app outage Belgium Train Services Train ticket purchases, digital announcements Media JOE, QMusic Banks and Post Services Airports Brussels, Charleroi France TV Channels TF1, TFX, LCI, Canal+ Systems Systems for the 2024 Paris Olympics Croatia Health and Air Traffic Central Health Information System, Air Traffic Control Germany Airports and Airlines Berlin Airport, Lufthansa Hospitals Hospitals in Lübeck and Kiel Hong Kong SAR Airports Hong Kong International Airport Airlines Cathay Pacific, Hong Kong Express, Hong Kong Airlines India Airlines Air India, Indigo, Akasa Air, SpiceJet, Vistara IT Firms Oracle, Nokia Israel Emergency and Health Magen David Adom, Hospitals: Sheba, Laniado, Rambam Services Israel Post, banks, pharmaceutical companies Malaysia Railway Services Railway operator KTMB’s ticketing system Netherlands Airports and Airlines Schiphol airport, Transavia Airlines Banks KNAB bank Government Government services, hospitals New Zealand Banks ANZ, ASB, Kiwibank, Westpac Supermarkets Woolworths, Foodstuffs Transport and Airports Auckland Transport, Christchurch Airport Philippines Various Services Banks, telecommunications, broadcasts, supermarkets Airlines Cebu Pacific flights South Korea Airlines Jeju Air Singapore Airports Changi Airport Spain Air Navigation Services ENAIRE’s Aena Switzerland Airports Zurich Airport United Kingdom Media Sky News, CBBC Airports Edinburgh, Gatwick Rail Companies Health Services NHS services Financial Services London Stock Exchange Retailers Ladbrokes Coral United States Airlines Ground stops for United, Delta, American Airlines Emergency Services 911 service outages in Alaska, Arizona, New Hampshire - The US Aviation Authority has mandated that all flights must land due to a technical computer glitch.
- Blue Screens at the Delhi Airport.
- Several federal agencies are affected by the incident, including the Department of Education, and Social Security Administration, which said Friday that it closed its offices as a result of the outage.
What is the IT problem?
CrowdStrike is a U.S.-based cybersecurity company with significant global technology market share. Its flagship product is Falcon, a software platform that organizations install on their computers to protect them from cyber-attacks and malware.
Falcon is essentially privileged software known as Endpoint Detection and Response (EDR). Its job is to monitor what is happening on the computers on which it is installed, looking for signs of nefarious activity (such as malware). If it detects something suspicious, it helps lock down the threat. To detect signs of an attack, Falcon must monitor computers in great detail, so it has access to many internal systems. This includes what communications computers are sending over the Internet, what programs are running, what files are being opened, and more.
Why did Falcon cause this IT problem?
When you install new software or apply any updates, the new product makes many changes to the Windows Registry. So, if the new software solutions have privileged access to a critical registry such as the kernel, device drivers, services, Security Accounts Manager, and user interfaces such as Falcon you have the perfect scenario for an IT geostorm called a Blue Screen of Death (BSOD).
CrowdStrike's latest update crashes Windows hosts associated with the Falcon sensor. And today's outage is a worst-case scenario.
How do I fix it?
Workaround Steps for individual hosts:- Reboot the host to give it an opportunity to download the reverted channel file. If the host crashes again, then:
Boot Windows into Safe Mode or the Windows Recovery Environment
NOTE: Putting the host on a wired network (as opposed to WiFi) and using Safe Mode with Networking can help remediation. - Navigate to the %WINDIR%\System32\drivers\CrowdStrike directory
- Locate the file matching "C-00000291*.sys“, and delete it.
- Boot the host normally.
Note: Bitlocker-encrypted hosts may require a recovery key.
- Option 1:
- Detach the operating system disk volume from the impacted virtual server
- Create a snapshot or backup of the disk volume before proceeding further as a precaution against unintended changes
- Attach/mount the volume to to a new virtual server
- Navigate to the %WINDIR%\System32\drivers\CrowdStrike directory
- Locate the file matching "C-00000291*.sys“, and delete it.
- Detach the volume from the new virtual server
- Reattach the fixed volume to the impacted virtual server
- Option 2:
- Roll back to a snapshot before 0409 UTC.
Why is this IT problem is a Cyber Threat?
This IT problem is not an attack BUT it's a cyber threat if your not fix the issue.
- CISA says it has observed threat actors exploiting this incident for phishing and other malicious activities.
- CISA urges organizations and individuals to remain vigilant and only follow instructions from legitimate sources.
- CISA recommends that organizations remind their employees not to click on phishing emails or suspicious links.
If you need assistance or would like to discuss your vulnerability status, please contact us.
